The CIA model applies to confidentiality, integrity, and availability as the best cybersecurity principles, describing a model that is designed to guide policies for information security within an organization or an agency. The model is sometimes referred to as the AIC (opposite of CIA) triad/model—which stands for availability, integrity, and confidentiality—to avoid confusion with America’s Central Intelligence Agency (CIA).
In this context, confidentiality refers to a set of broad guidelines that restrict access to all types of data and information as needed. Integrity is the guarantee that the information is trustworthy and accurate. And availability is a risk management strategy that ensures authorized individuals have accurate and reliable access to information.
What are the three main components of the CIA triad/model?
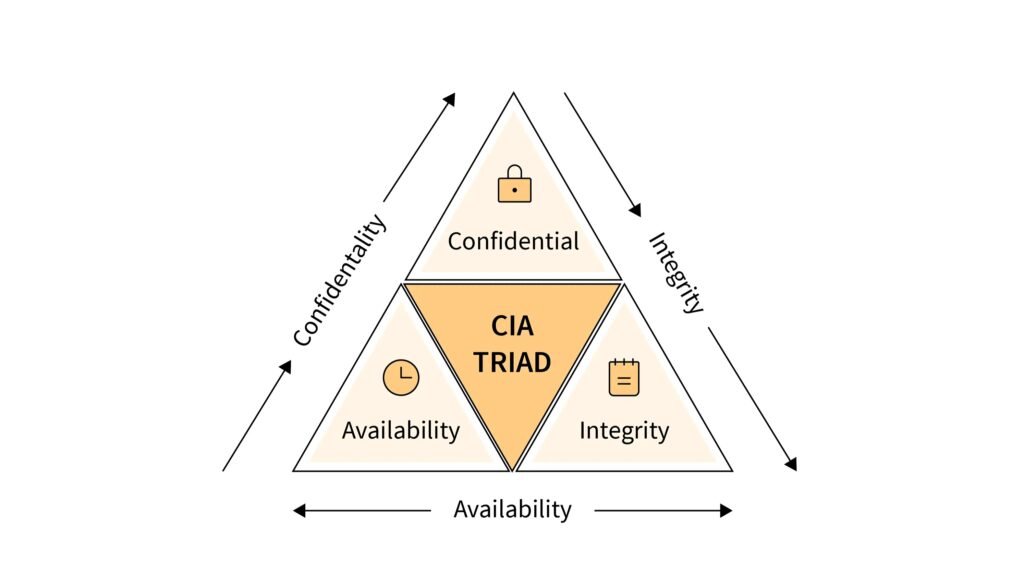
The CIA triad’s components are broken down as follows:
- Confidentiality: Similar to privacy, confidentiality measures are intended to protect sensitive information from unauthorized access attempts. Data is commonly classified based on the amount and type of damage that could be caused if it falls into the wrong hands. More or less stringent data security measures can then be implemented in accordance with those categories.
- Integrity: Data must be consistent, accurate, and trustworthy throughout its entire lifecycle. Data must not be changed while in transit, and steps must be taken to prevent unauthorized people from altering it, such as in data breaches.
- Availability: Information should be consistently and easily accessible to authorized parties. This includes properly maintaining the hardware, technical infrastructure, and systems that store and display the data.
Why does the CIA triad matter?
Each letter in the CIA triad represents a fundamental concept in cybersecurity. The security model’s importance speaks for itself: confidentiality, integrity, and availability are regarded as the three most important concepts in information security.
These three principles, when considered together within the triad framework, guide the development of organizational security policies. When assessing the needs and use cases for potential new products and technologies, the triad enables organizations to ask targeted questions about how value is delivered in those three key areas.
Detailed Examples of the CIA Triad/Model (Videos)
Benefits of the CIA triad
The CIA triad offers numerous advantages to businesses, particularly those that deal with sensitive data. The benefits of triad implementation include the following:
- Comprehensiveness: Because of the three elements, security teams are more focused on guaranteeing the availability and accuracy of their data than they are on stopping attackers.
- Data security and privacy: Data security and privacy include being prepared against cyber attacks and unauthorized access to your valuable data.
- Compliance: It ensures the confidentiality, integrity, and availability of sensitive information, meaning the rules and legal structures that are to safe information.
- Proactive risk prevention: When correctly implemented, the triad creates an environment.
Best practices for implementing the CIA triad
When implementing the CIA triad/model, an organization should adhere to a general set of best practices. These are divided into three subjects, which include the following:
- Confidentiality
- Use encryption and two-factor authentication (2FA).
- Follow an organization’s data management security policies.
- Integrity
- To reduce human error, ensure that employees understand compliance and regulatory requirements.
- Utilize backup and recovery software and services.
- Make use of version control, access control, security control, data logs, and checksums.
- Availability
- Use security measures like redundancy, failover, and RAID.
- Ensure that systems and applications are kept up to date.
- Use network or server monitoring tools.
The History of the CIA Model/Tried
The CIA triad is not made by one person. It is a way to protect information. Here are some more details on the creation of the CIA Model:
- Confidentiality: This word was used in computer science in 1976. It means keeping information private.
- Integrity: In 1987, two researchers talked about it in a paper. It means keeping data correct and honest.
- Availability: This idea became popular in 1988. It means making sure information is easy to get when needed.
By 1998, people started calling these three ideas the CIA triad. Later, a researcher named Donn B. Parker added more parts to it, like authenticity (proving something is real).
For more than 20 years, the CIA triad has helped keep computers safe. Some experts now think it needs to change to keep working well.
Challenges of the CIA Triad
The CIA are the rules for keeping information secured. But it can be too hard to follow them all the time.
- Confidentiality means keeping things secret. Hackers might attempt to steal private information, such as passwords. To stay safe, people should use strong passwords and be careful online.
- Integrity means keeping information correct. If someone changes it by mistake or on purpose, it can cause problems. For example, if school grades are changed, it won’t be fair.
- Availability means people need to use the information when they need it. If a website breaks or stops working, it’s hard to get things done.
Keeping the CIA Triad is not easy, but it is important. We need to stay careful and use tools to protect our information.
Real-World Examples
We see many things around us that are real-world examples. For example, a clock tells us the time. It is something we use every day. Another example is a car. Cars take people from one place to another.
When you turn on a light, it is another real-world example. The switch helps the light work. This shows how simple tools make life better.
Even your school bag is a real-world example. It holds your books, pencils, and lunch. It helps you stay organized and ready for school.
Look around you! Your house, the park, and even your toys are real-world examples. They are all things that make life fun and easy.
Real-world examples are all around us. They help us understand how things work in the world.
Summarization and FAQs
The CIA triad is like a superhero team for computers! Its job is to protect information so it will be safe, correct, and easy to find. Each model has a special power to help.
Confidentiality is like a secret keeper: Imagine your diary has a lock, and only you have the key. Confidentiality keeps secrets safe by letting only the right people see them. For example, passwords protect your computer so no one can sneak in.
Integrity is the Story Protector: Imagine writing a story for school. What if someone changed your happy ending? Integrity makes sure the story stays just how you wrote it. It checks that nothing gets messed up.
Availability is the always-open librarian: Imagine needing a book from the library, but it’s locked up. Availability makes sure the library (or information) is always open when you need it.
Cool tools like passwords, backups, and codes help the CIA Model. They fight hackers, fix mistakes, and stop accidents from ruining the day.
What is the CIA method?
The three letters in the phrase “CIA triad” stand for confidentiality, integrity, and availability. The CIA triad is a commonly used model for developing security systems. They are used to identify vulnerabilities and methods for developing solutions.
What is the formula for the CIA?
Nesbitt and Young (1982) developed the Chemical Index of Alteration (CIA) to quantify weathering history recorded in sediments and sedimentary rocks. CIA is defined as Al2O3/(Al2O3 ⑹ CaO* ⫹ Na2O ⫹ K2O) ⫻ 100 (molar contents, with CaO* representing the CaO content in the sample’s silicate fraction).


